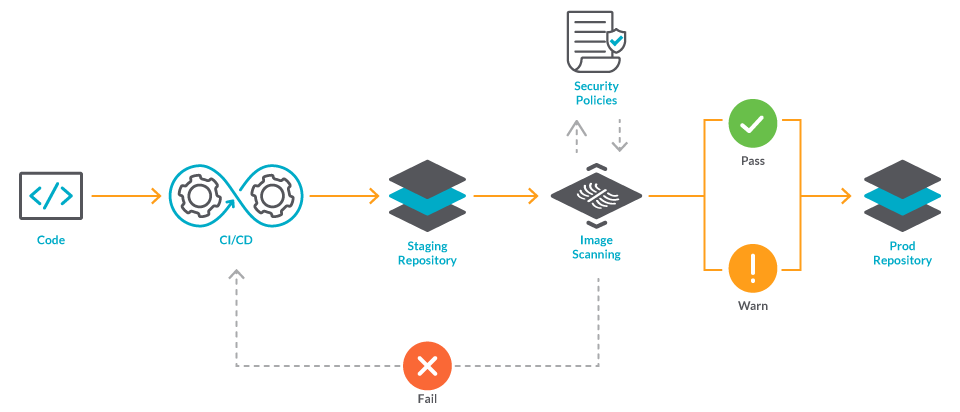
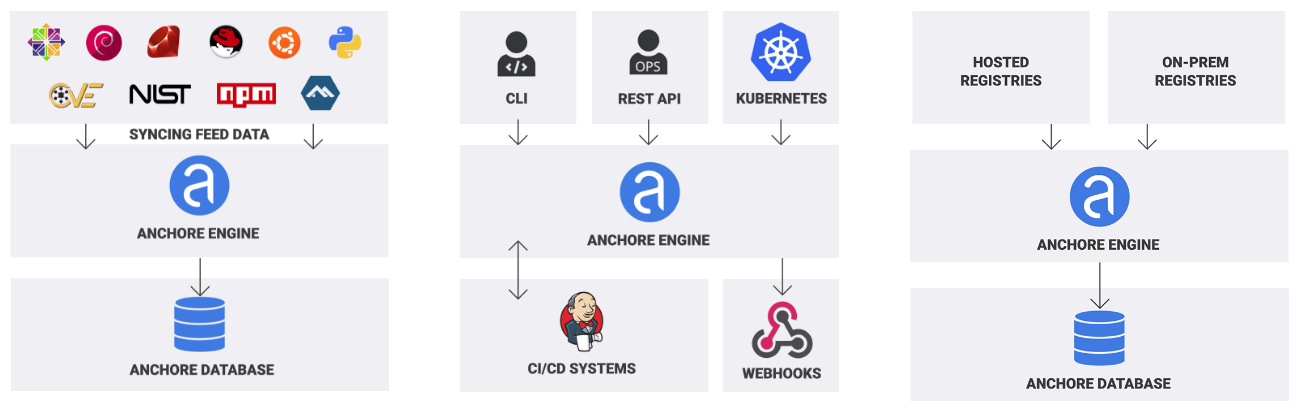
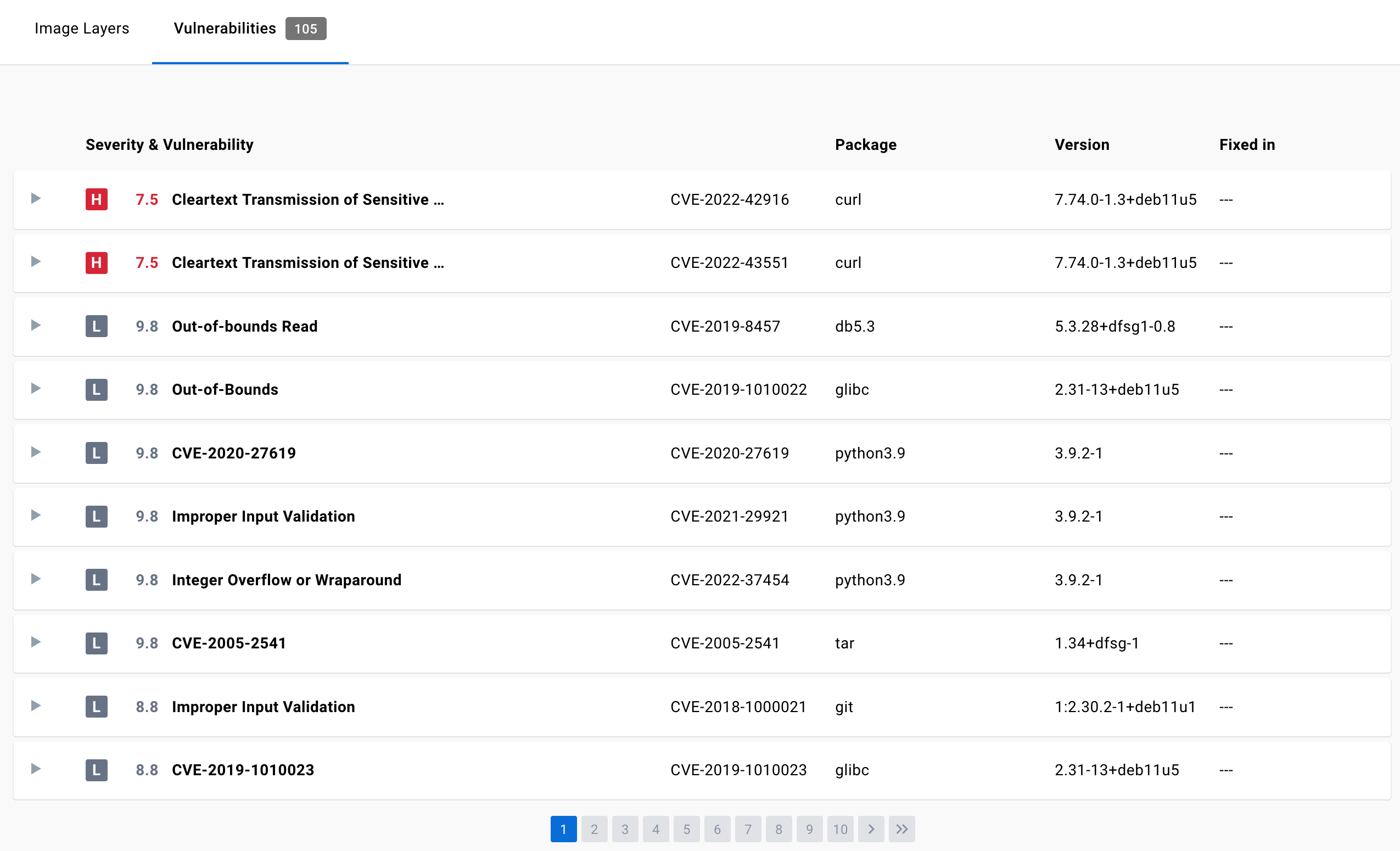
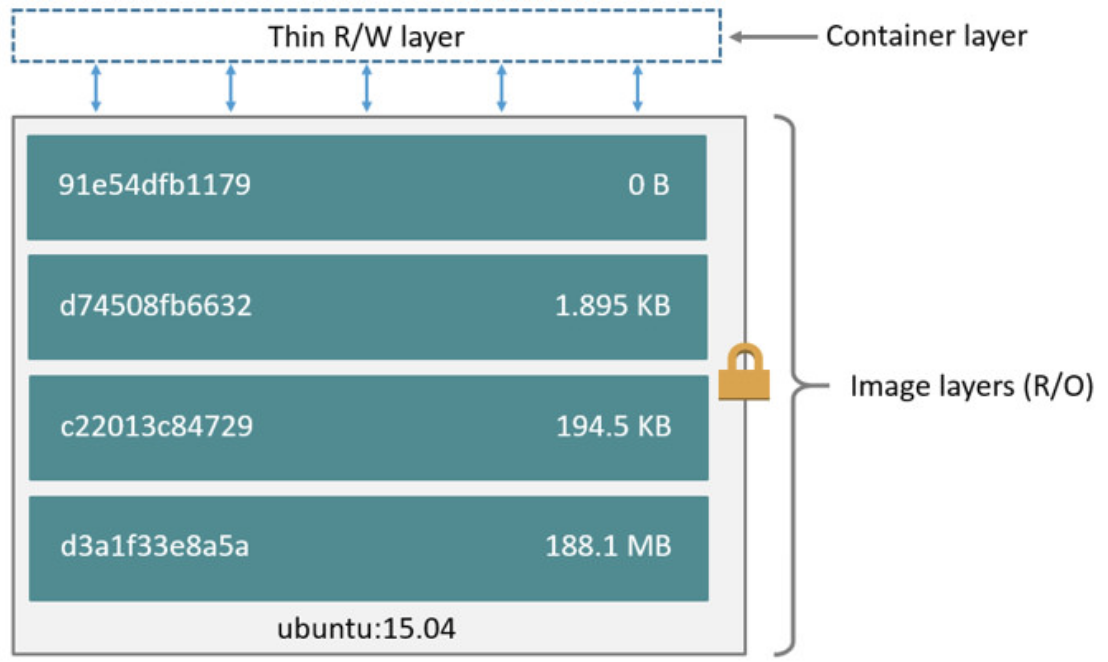
Part 1 - Quick look at CICD Integration in Azure Security Center to scan your docker image -Notes of Azure Security + Governance

Docker - We're making it easier than ever to deploy vulnerability scanning along multiple points of your development. Read more https://dockr.ly/36kIHBW #ContainerSecurity #Docker @snyksec | Facebook

How to scan vulnerabilities for Docker container images — Part2 | by Luke Skywalker | System Weakness

Scanning Docker Images for Vulnerabilities using Clair, Amazon ECS, ECR, and AWS CodePipeline | AWS Compute Blog

Integrating Docker Container Vulnerability Scans in CI Builds | by Tanmay Deshpande | Better Programming

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog

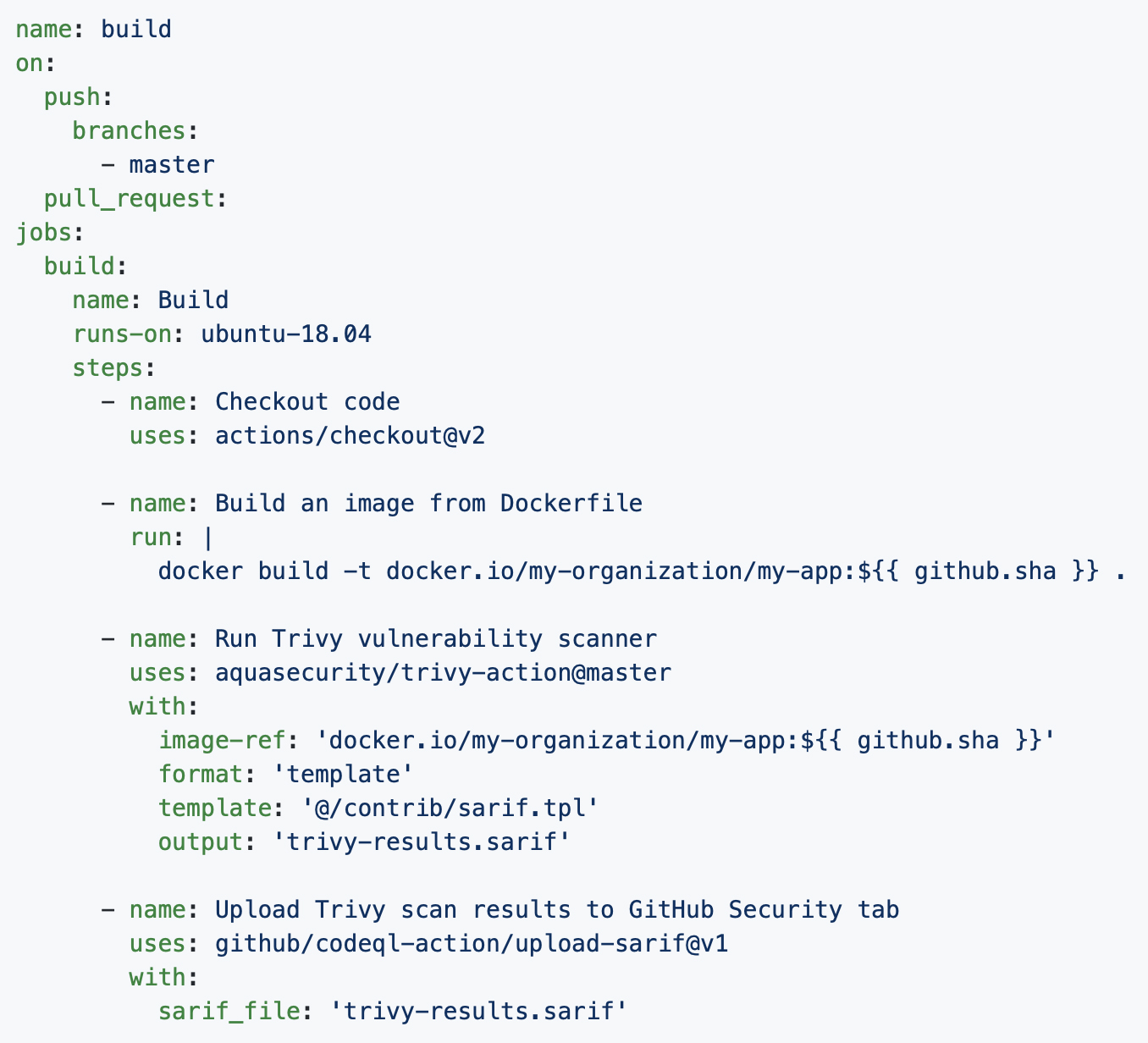
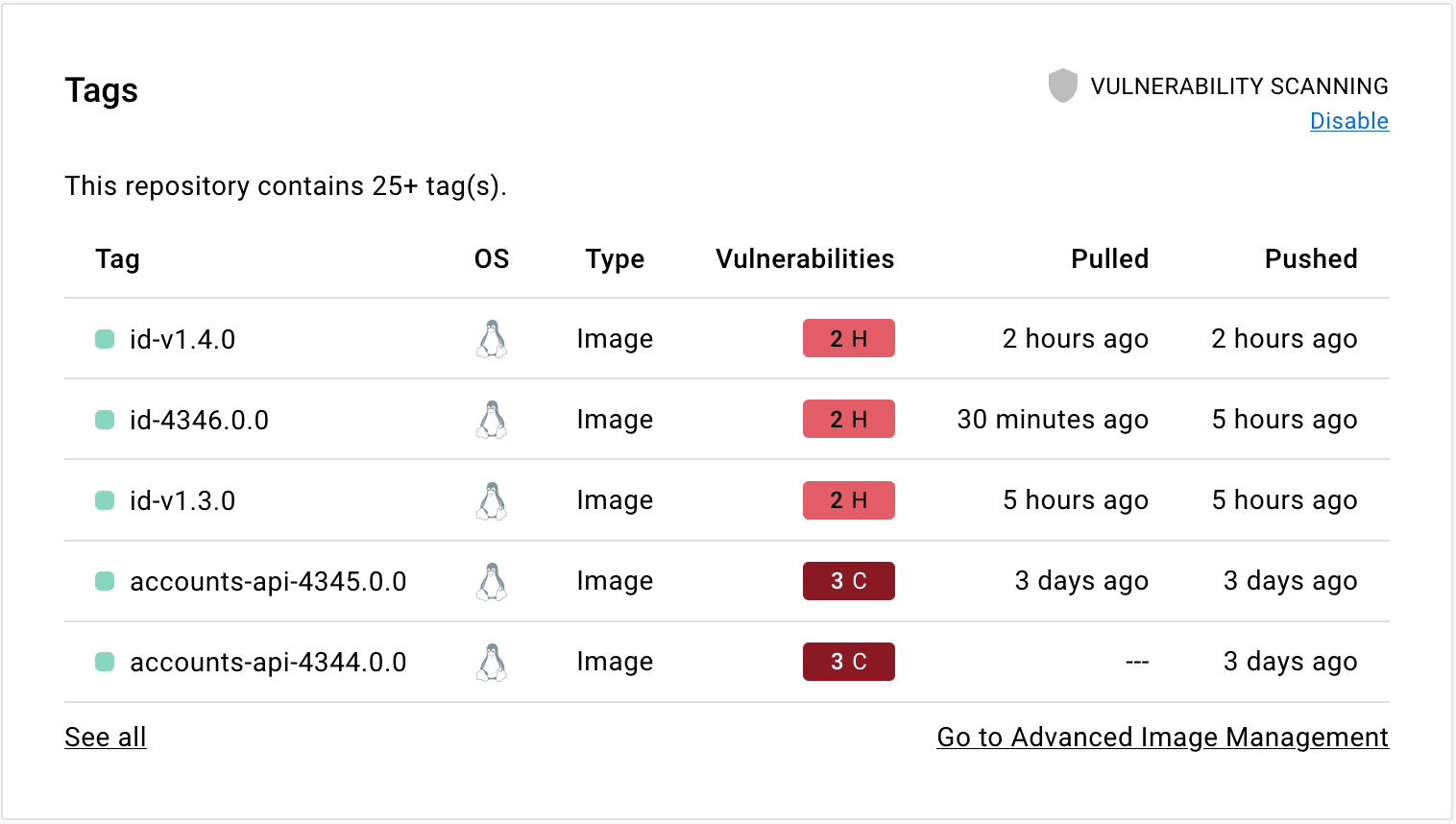
/filters:no_upscale()/news/2020/12/dockerhub-image-vulnerabilities/en/resources/1Screenshot%20from%202020-12-20%2014-54-56-1608456415853.png)